I’m often asked, “what do you actually do for our hosting fee?”. For those clients that pay purely for hosting, and not for other digital marketing services, when you are not technical, it’s a difficult question to answer.
The easiest analogy is changing the oil in your car. You don’t have to. You can drive your car until it bursts into flames, or, you can maintain your car, and have a more reliable vehicle. There.. nothing “techy” to digest. With “el cheapo hosting” you get a place to put your site. It’s up to you to provide the maintenance. With HOF, we take care of it.
The news yesterday was bad. There was an attack on millions of websites, all WordPress, all focus on some of the little bits of software that run on a site. Every time something like this happens, or every time the potential for something like this to happen, most software developers will update their software. Your website relies on anywhere from a dozen, to hundreds, of little independent pieces of software, and each software has its own update schedule.
Those sites that were updated, withstood yesterday’s attack with no issues. Those sites that were not, could be crippled. The attack gave anyone the ability to become an administrator of a compromised site. Horrific!
Here’s a full accounting of the attack. The detailed article is provided by WORDFENCE, one of the premier tools for stopping hacks and keeping sites updated.
None of our sites were impacted by this attack.
Jeff
|
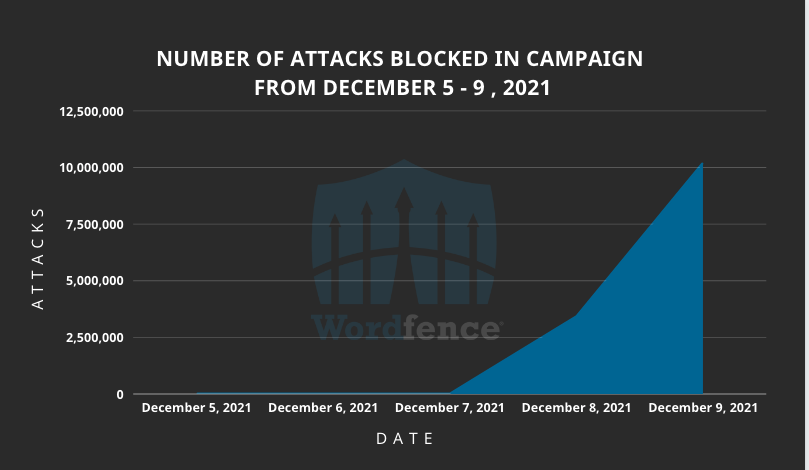
Today, on December 9, 2021, our Threat Intelligence team noticed a drastic uptick in attacks targeting vulnerabilities that make it possible for attackers to update arbitrary options on vulnerable sites. This led us into an investigation that uncovered an active attack targeting over a million WordPress sites. Over the past 36 hours, the Wordfence network has blocked over 13.7 million attacks targeting four different plugins and several Epsilon Framework themes across over 1.6 million sites and originating from over 16,000 different IP addresses. A Closer Look at the Attack DataAttackers are targeting 4 individual plugins with Unauthenticated Arbitrary Options Update Vulnerabilities. The four plugins consist of Kiwi Social Share, which has been patched since November 12, 2018, WordPress Automatic and Pinterest Automatic which have been patched since August 23, 2021, and PublishPress Capabilities which was recently patched on December 6, 2021. In addition, they are targeting a Function Injection vulnerability in various Epsilon Framework themes in an attempt to update arbitrary options. In most cases, the attackers are updating the users_can_register option to enabled and setting the default_role option to `administrator.` This makes it possible for attackers to register on any site as an administrator effectively taking over the site. Our attack data indicates that there was very little activity from attackers targeting any of these vulnerabilities until December 8, 2021. This leads us to believe that the recently patched vulnerability in PublishPress Capabilities may have sparked attackers to target various Arbitrary Options Update vulnerabilities as part of a massive campaign. |
|
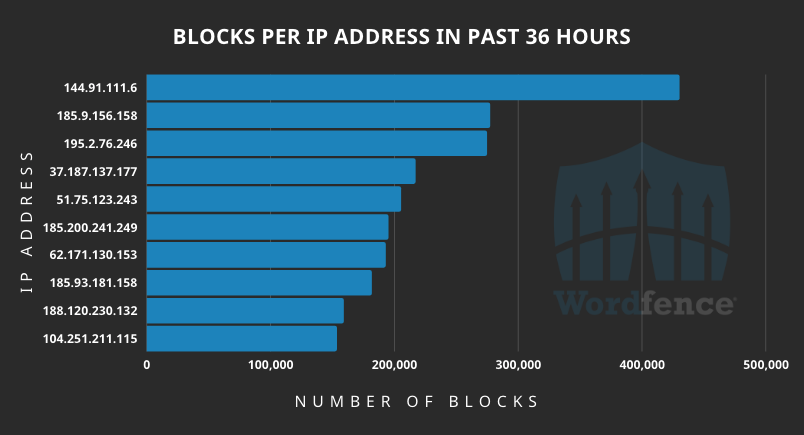
The top 10 offending IPs over the past 36 hours include:
|
How Can I Keep My Site Protected?Due to the severity of these vulnerabilities and the massive campaign targeting them, it is incredibly important to ensure your site is protected from compromise. We strongly recommend ensuring that any sites running one of these plugins or themes has been updated to the patched version. We have the affected versions of each product outlined below. Please ensure that your sites are running a version higher than any of the ones listed. Simply updating the plugins and themes will ensure that your site stays safe from compromise against any exploits targeting these vulnerabilities. The following are the affected plugins and their versions:
The following are the affected Epsilon Framework theme versions:
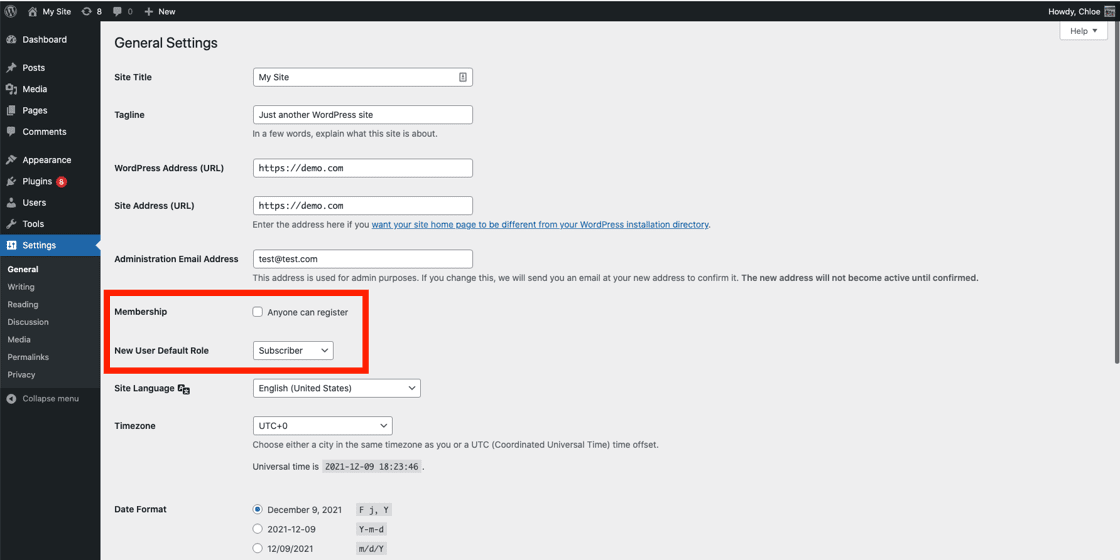
How Do I Know If My Site Has Been Infected and What Should I do?As previously stated, the attackers are updating the users_can_register option to enabled and setting the default_role option to `administrator` in most cases. To determine if a site has been compromised by these vulnerabilities, we recommend reviewing the user accounts on the site to determine if there are any unauthorized user accounts. If the site is running a vulnerable version of any of the four plugins or various themes, and there is a rogue user account present, then the site was likely compromised via one of these plugins. Please remove any detected user accounts immediately. It is also important to review the settings of the site and ensure that they have been set back to their original state. You can find these settings by going to the /wp-admin/options-general.php page. Please make sure the `Membership` setting is correctly set to enabled or disabled, depending on your site, and validate that the `New User Default Role` is appropriately set. We strongly recommend not using `Administrator` for the new user default role as this can lead to inevitable site compromise.
|
|
Please review this guide to cleaning a hacked site with Wordfence to complete the clean of the site once the intrusion vector has been determined and the immediate issues have been resolved. If the entire site is not scanned and cleaned to ensure there are no additional backdoors, it may be possible for an attacker to regain access to the site. ConclusionIn today’s post, we detailed an active attack campaign targeting various plugins and themes that make it possible for attackers to effectively take over vulnerable sites through the use of arbitrary option updating. We strongly recommend ensuring that all of your sites have been updated to the patched versions of the affected plugins and themes. You can also find this post on the official Wordfence blog if you’d like to share it with the larger community. |


Recent Comments